The Backwards Alphabet Code is very simple All you have to do is make a list of all the letters in the alphabet, and then make another list right next to it, of all the letters in backwards order Kind of like this A = Z B = Y C = X D = Wand so on, through the alphabetEnigma decoder Decrypt and translate enigma online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Decimal to text Base32hex Reverse text 24 August 21 Codewords are like crossword puzzles but have no clues!

Enigma 37 Encryption Machine With Letters Numbers Encode And Etsy
Enigma code alphabet
Enigma code alphabet- The Germans began using the Enigma machine in the late 19s By late 1932, the Poles had broken the Enigma code In 1939 just a matter of weeks before Hitler invaded Poland, the Polish Cipher Bureau shared its technology with the French and the British, who continued to decode messages Each number in this puzzle represents a letter of the alphabet Solve our Enigma code by correctly allocating each letter to its corresponding number All letters of the alphabet are used The Enigma code is set in a crossword format, each row or column will spell a word when completed correctly We have given you a starting either a letter or




File Enigma Rotors With Alphabet Rings Jpg Wikimedia Commons
Enigma, first contacts From 1928 the German army Wehrmacht started to test a new cipher system This caused panic in the ranks of the Polish Secret Service After the end of the First World War France and Great Britain believed that Germany was no longer a threat to their security However, Poland never shared this opinion Solving the EnigmaTo encrypt your message with an Enigma machine, you would simply In wigwag code, messages were spelled out according to a letternumber code Each letter of the alphabet was represented by a combination of numbers, and the numbers corresponded to flag movement A movement to the left of the center meant a "1," and a movement to the right of center meant a "2" The Enigma code, a very
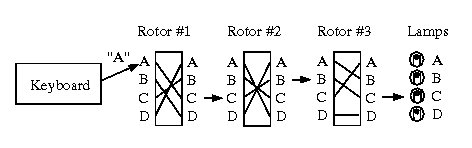
Enigma – a polyalphabetic substitution cipher machine The Enigma machine created a different cipher alphabet for every consecutive letter of plaintext Two important characteristics were the result of the socalled reflector, which we will look at in more detail later (1) the alphabet was reciprocal and (2) a letter could never be encoded The Enigma code was first broken by the Poles, under the leadership of mathematician Marian Rejewski, in the early 1930s In 1939, with the growing likelihood of a German invasion, the Poles turned their information over to the British, who set up a secret codebreaking group, known as Ultra, under mathematician Alan M TuringSimplified Enigma machine that is limited to a six letter alphabet Figure 4 Simplified version of a Enigma machine with one rotor The disk on the left is the keyboard, the middle ring is the rotor, and the disk on the right is the lampboard The wiring of the rotor determines how the plaintext letters will be encrypted
The Principle of the Enigma Tony Sale's Codes and Ciphers one for each letter of the alphabet, connecting a battery to the top letter terminal where the key is pressed Continue to the next page to see how the Enigma was put together and how it was given a further layer of complexity for German military use This page was created byGet Secret Agent / Spy Party ideas Your mission Throw your child a great spythemed birthday partyThey altered from alphabetical order, to leaving out letters of the alphabet, to even broadcasting bogus code groupings The earliest Polish work on the German machine cipher had begun in , a short while after the system had been introduced by the German Navy and Army
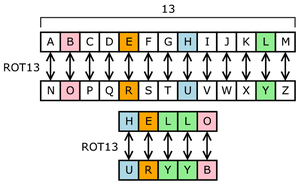



Substitution Cipher Wikipedia



Enigma Codeproject
This code simulates the Enigma machine, minus the plugboard Here's some test code that illustrates how the machine's construction and use (string) encipherings for the machine's alphabet offset (int) the starting position of the rotor """ def __init__(self, mappings, offset=0) selfinitial_offset = offset selfreset() selfforwardEnigma Enigma was a ciphering (code communication) system used by the German military from 1926 until the end of World War II, and by several other nations for some years after Enigma was the first mechanized messageencryption system to see wide use Enigma produced such thoroughly scrambled messages that for many years its cipher was Deciphering the Enigma Code of the Brain One of the current challenges of neuroscience is to decipher the neural code, the language of the brain that is translated into movement This is a fundamental step to be able to program devices that allow paralysis to be treated and to produce a new generation of prostheses
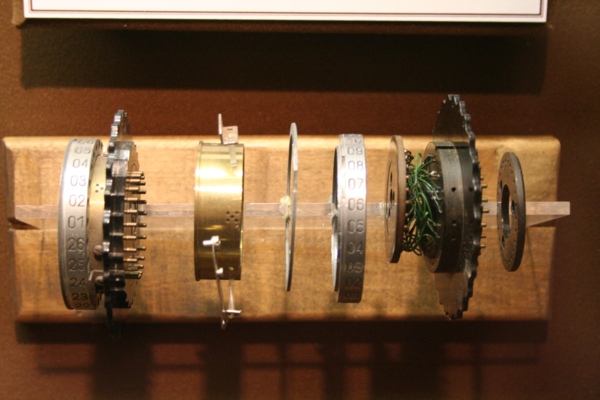



Enigma Rotor Details Wikipedia



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
The standard military ENIGMA used three 26point wired metal and black plastic rotors selected from a set of five to eight Each rotor was a cylinder with a large, moveable notched wheel on one end with an alphabet (or numbers) around its circumference One face of the cylinder had twentysix springloaded copper pins protrudingSYMBOLS CIPHERS CODES CRYPTO CHARTS GRAPHS See more ideas about ciphers and codes, charts and graphs, symbolsConverts alphabet characters into their corresponding alphabet order number (eg A=1, B=2, , Z=26) while nonalphabet characters are being dropped Reverse text Swiss Enigma AES Encryption Binary to English Morse code to text




The Enigma Enigma How The Enigma Machine Worked Hackaday



The Enigma Machine And The Ultra Secret South African Military History Society
Incandescent Alphabets is a remarkable look at the intersections between language and psychosis Rogers extends our understanding of madness beyond the biomedical model, and delivers a view of psychosis that is rooted in a deep respect for the human spirit and each individual's experience For thousands of years, ciphers have been used to hide those secrets from prying eyes in a catandmouse game of codemakers versus codebreakers These are some of history's most famous codes 1To start you off, we reveal the codes for two or three letters



Cryptology I Vigenere Based Systems



Investigations Enigma
The real Enigma has this table fixed inside the wooden cover of the machineThe Enigma rotor cipher machine was potentially an excellent system It generated a polyalphabetic substitution cipher, with a period before repetition of the substitution alphabet that was much longer than any message, or set of messages, sent with the same key A major weakness of the system, however, was that no letter could be enciphered to itselfThe Wehrmacht Enigma has rotors with numbers Therefore, to set a message key in the next step, Step 6, the simulator has a help sheet to convert letters to numbers This sheet appears when you click on the number inside the little rotor window 17 Do this now!



Why Did Enigma Machines Use Multiple Rotors Quora




Enigma Codeproject
The encryption code returns an element from the alphabet array The Caesar cipher is probably one of the most basic ciphers, although it was the basis of the Enigma code In 1923, the German Navy used its own Enigma machine and by the 1930s, it became standard equipment by the German Intelligence divisions In October 13, a 1944 German Enigma machine wasTeleprinter Code International Teleprinter Code (also known as BaudotMurray Code) enables messages to be sent as a series of electrical impulses Each letter of the alphabet is represented as a 5 bit code comprised of impulses or the absence of




Who Was Alan Turing Alan Turing Was A



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
The enigma machine was used in World War II to encrypt secret messages The Enigma machines are a series of electromechanical rotor cipher machines The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication Enigma machines becameInstead, every letter of the alphabet has been replaced by a number, the same number representing the same letter throughout the puzzle All you have to do is decide which letter is represented by which number!For the Alphabet Code To accompany the book Enigma, by Graeme Base Below is the key to the alphabet code for this book To crack this code, readers need to turn the three dials to show the correct symbols Those symbols are hidden in one of the pictures in the bookthe photo of Grandpa and Bertie on page 29




I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine




Enigma 1261 It S All Greek To Us Enigmatic Code
Alphabet, let's take another look into the Enigma machine The Enigma as Matrices The Enigma is not a monoalphabetic cipher, but a polyalphabetic cipher This is a result of the rotor movements mentioned above Imagine a linear function E maps R26 to R26, althoughFigure 4 details of an Enigma rotor (1) The finger notches used to turn the rotors to a start position (2) The alphabet RING or tyre round the circumference of the rotor (see below for an explanation of its significance) (3) The shaft upon which the rotors turn (4) The catch which locks the alphabet ring to the core (5) (5) The CORE containing the crosswiring between contactsEncryption with Caesar code is based on an alphabet shift (move of letters further in the alphabet), it is a monoalphabetic substitution cipher, ie a same letter is replaced with only one other (always the same for given cipher message) The most commonly used shift/offset is



If We Use The Current Computing Technology Would We Be Able To Crack The German Ww2 Enigma Code Without Knowing Any Information About The Code Quora




How The Enigma Works Nova Pbs
Hugh SebagMontefiore, the author of Enigma The Battle For The Code (04), that without this information the substantial breaks into German Army and Air Force Enigma ciphers by the British would have occurred several years later (17)Code Wheel for encrypting and deciphering messages This activity can be easily differentiated to accommodate different ages and abilities The idea is to use two circles to create a Code Wheel to encrypt and decipher messages What you need Easier version Circle Templates printed on card Scissors Pencils/pens Split pins Harder version CardCode Breaking and Decoding Tools The following codes and ciphers are detailed below, click to go straight to one or carry on reading Modern Codes, Atbash Cipher, Caesar Shift, Caesar Square, Anagrams, Substitution Ciphers, Other Ciphers Creating and decoding secret messages has played a pivotal role throughout history and in many fictional novels, from the Caesar Cipher by




Enigma Codeproject



Enigma Procedure
The enigma rotors The rotors are special gears with 26 pins Every pin is related to an English letter When an electric signal (in mechanical machine) comes to Another enigma that surrounds the Polish alphabet are the phantom letters Q, V and X They're not in the language, but they show up from time to time and this confuses me V, for instance, isn't in the written language, but does exist in body language – I've seen many Poles holding up two fingers to show the V for victory gestureSecret codes, high security, everyone knows the password to fun is 'spy party'!
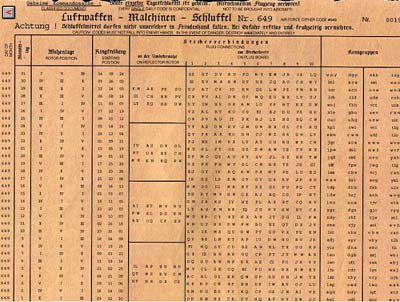



Exploring The Enigma Plus Maths Org



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
Http//wwwsupercomputingchallengeorg/0607/finalreports/63pdf How do you write an enigma code? Enigma allowed an operator to type in a message, then scramble it by means of three to five notched wheels, or rotors, which displayed different letters of the alphabetEnigma's Secrets How it Worked and How the Code was Broken By way of introduction, see the Historical Background to Enigma and the Key Players Involved The Working Principle The Enigma machine basically provided a simple substitution of a plaintext symbol with a different ciphertext symbol generated by the machine What made the machine special however was that



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf




The Enigma Machine The National Museum Of Computing
An Enigma machine is a famous encryption machine used by the Germans during WWII to transmit coded messages An Enigma machine allows for billions and billions of ways to encode a message, making it incredibly difficult for other nations to crack German codes during the war — for a time the code seemed unbreakable Alan Turing and other researchers exploited a The key to a successful simulation of the ENIGMA machine is to know the internal wirings of the rotors (or "wheels"), shown below The rotors are labeled I through VIII, b, and g The letters of the alphabet in order represent the input, and the wiring for each rotor indicates the transformation for each letterClassic Ciphers In cryptography, a cipher (or cypher) is a method for protecting data through encryption and decryption Most ciphers require a specific key for encryption and decryption, but some ciphers like the ROT13 or Atbash ciphers have fixed keys Many of the ciphers listed here were for military or other significant use during an



Description Of The Enigma




The Enigma Cipher Machine And Breaking The Enigma Code
One would wonder why the encryption mattered anyway, and why it took a lot of effort to decode it The quality of codes is determined by the number of possibilities of getting the correct answer In the case of the Enigma code, one had to get all settings on the Enigma machine right before you could decode itM_key = alphabet r randint (0, 25) alphabet r randint (0, 25) alphabet r randint (0, 25) cipher = enigma encipher (m_key m_key) # Take the cipher text and add it to the alphabet set for day key AD cipher 0 = cipher 3 if AD cipher 0 is None else AD cipher 0 BE cipher 1 = cipher 4 if BE cipher 1 is None What Made the Enigma Code Special?




The Human Errors That Defeated Enigma Openmind



The Polish Attack On Enimga
The Enigma was constantly updated throughout the war, so the exact types of settings variedHowever, they usually included The rotors The Enigma M1 had three rotors that the operator could choose from from a pool of 5, though this number was later increased to 8 (and a machine with 4 rotor slots was released toward the end of the war) You




The Enigma Cipher Machine And Breaking The Enigma Code




11 Cryptographic Methods That Marked History From The Caesar Cipher To Enigma Code And Beyond




10 Codes And Ciphers Commonly Used In History Ciphers And Codes Coding Cryptography




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium




Pin On Cryptography




Enigma Rotor Diagram Created By Wapcaplet In Blender Cc By Sa 3 0 Download Scientific Diagram




The Enigma 2




Ic211 Oop And Enigma



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher




How Did The Enigma Machine Work Computing The Guardian
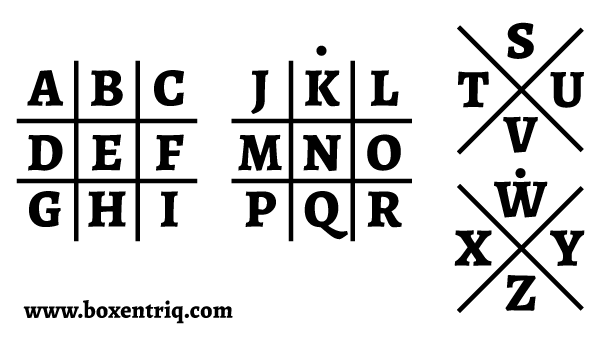



Pigpen Cipher Online Tool Boxentriq



Enigma Cipher



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf




Charlesreid1



If The Allies Were Able To Steal An Enigma Machine I Assume They Also Stole A Code Book Then Why Did They Still Have To Break The Code Quora



The Polish Attack On Enimga




The Enigma 1




Codes And Ciphers Puts Students To Test Bryn Mawr Alumnae Bulletin



1




Enigma Rotor Details Wikipedia




Enigma 37 Encryption Machine With Letters Numbers Encode And Etsy
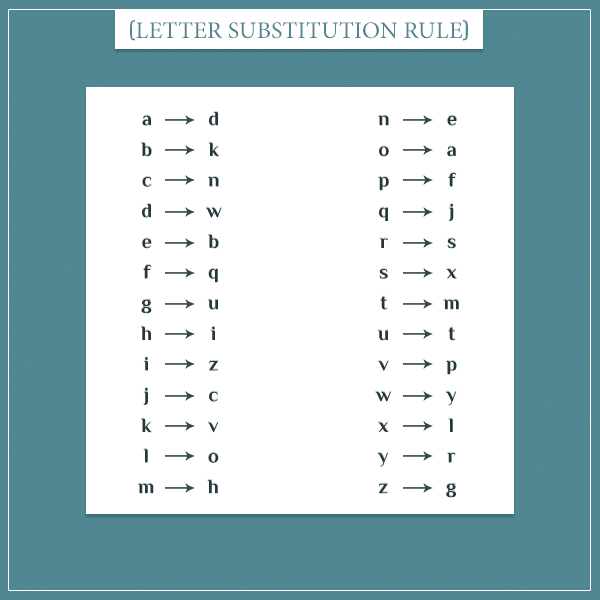



Cryptography Historical Introduction Combinatoric Analysis Series Probabilistic World



1




How To Build An Enigma Machine Virtualisation In Python By Vasile Păpăluță Analytics Vidhya Medium



1




The Enigma Machine On The Centenary Of The Man Who Brought It Down The Verge




Enigma 419 Painting By Numbers Enigmatic Code
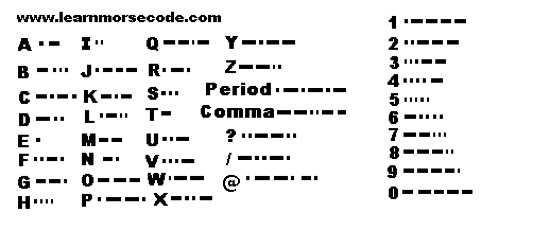



Top 10 Codes And Ciphers Listverse




Zahlwerk Enigma




Cryptanalysis Of The Enigma Wikiwand



1




Braille Alphabet Board Teaching Braille To The Sighted



Enigma The German Cipher Machine




It S A Cipher For Fez Ciphers And Codes Alphabet Letters
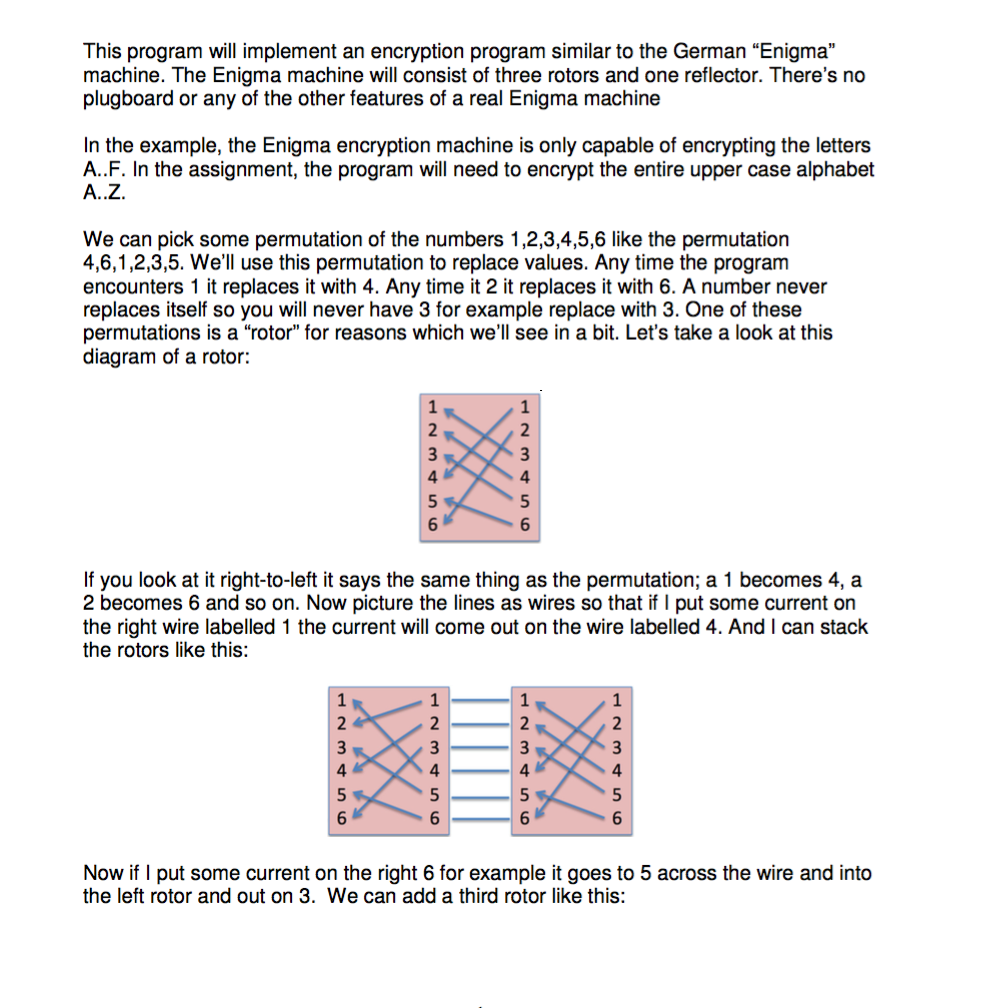



This Program Will Implement An Encryption Program Chegg Com




Linear Algebra In Cryptography The Enigma Machine
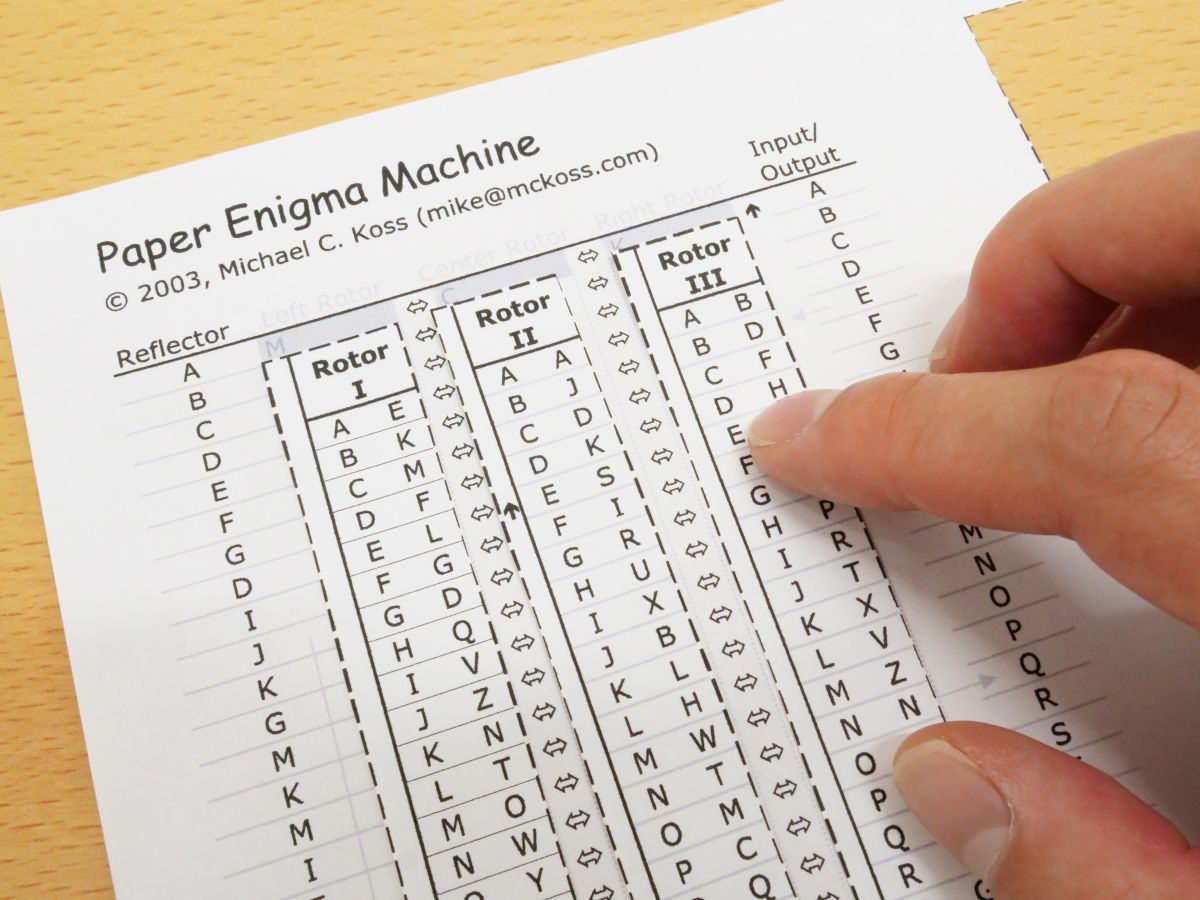



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine




File Enigma Rotors With Alphabet Rings Jpg Wikimedia Commons



Red Luth Riddle Tools
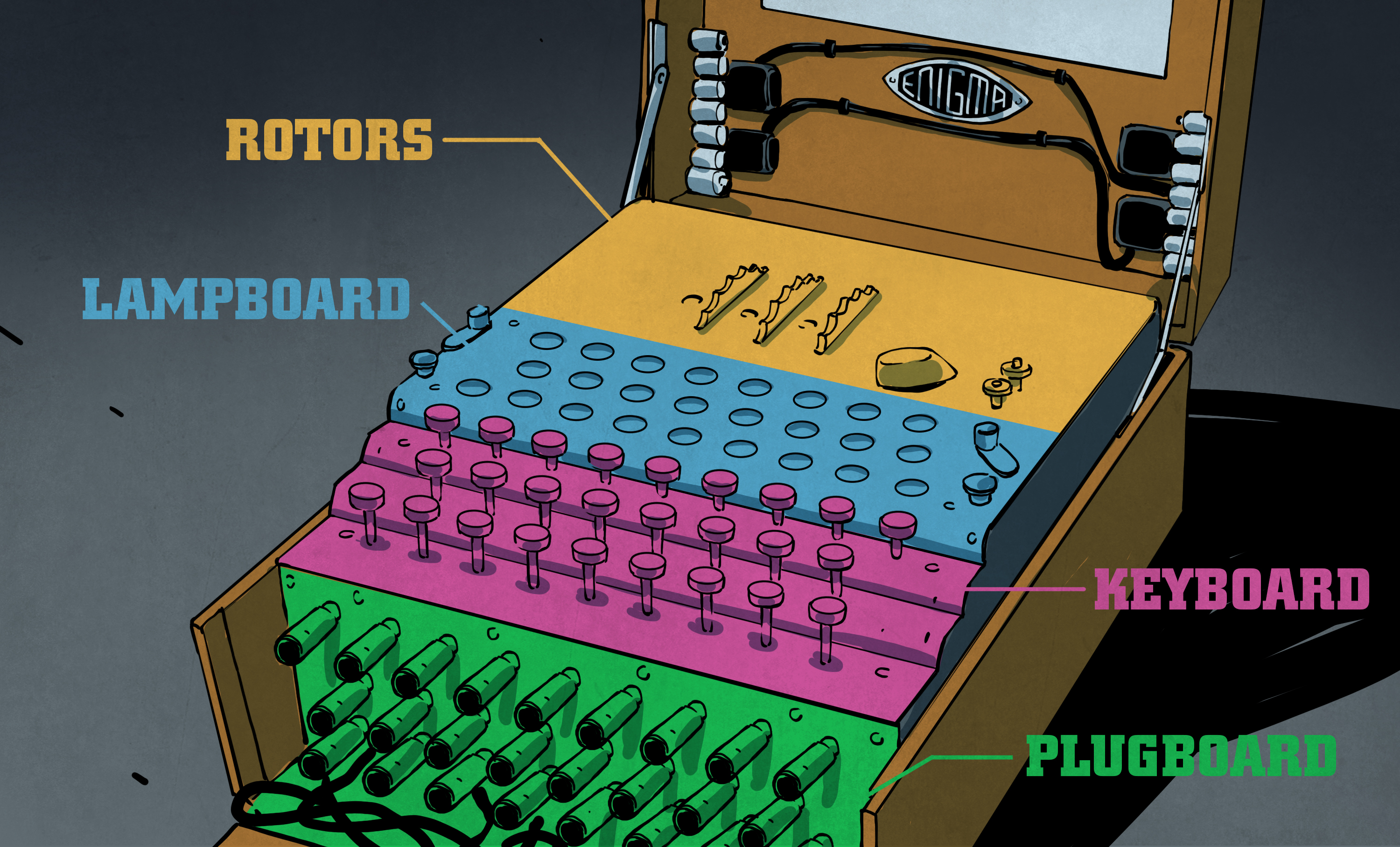



The Enigma Enigma How The Enigma Machine Worked Hackaday



The Enigma Machine And The Ultra Secret South African Military History Society




Cryptanalysis Of The Enigma Wikipedia




Hobo Signs Richard Gallon We Are Here
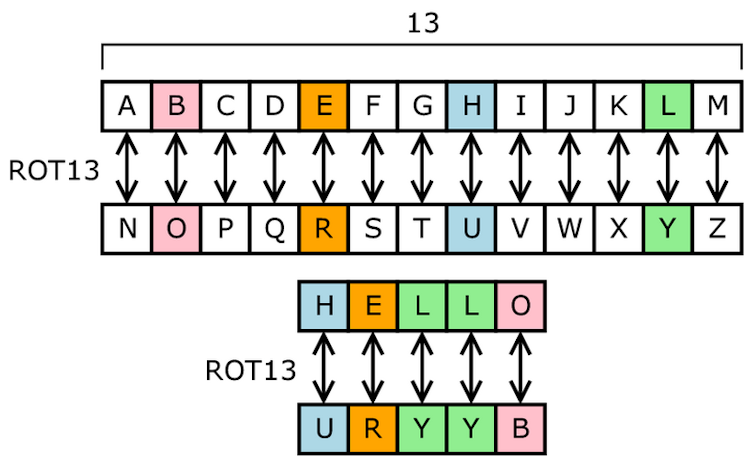



Codebreaking Has Moved On Since Turing S Day With Dangerous Implications




Rotor Machine Wikiwand




Enigma Machine Wikipedia



Enigma Procedure



Enigma C



The Polish Attack On Enimga
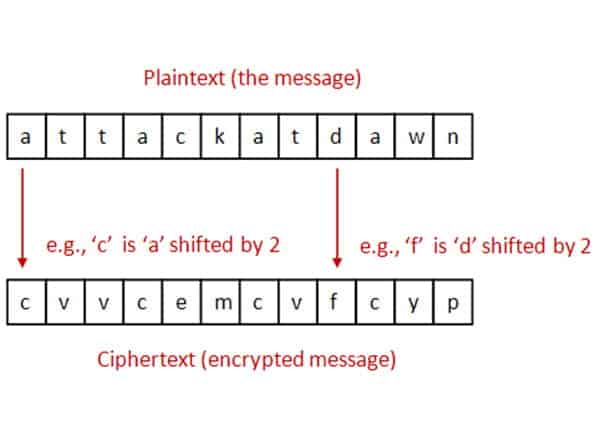



How To Make And Use Cipher Wheel Stem Little Explorers
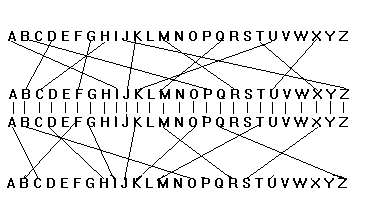



The Enigma 1
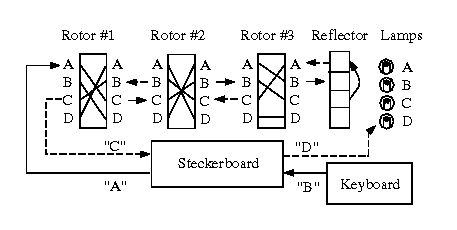



Cryptology I Vigenere Based Systems




10 Codes And Ciphers Commonly Used In History Coding For Kids Secret Code Ciphers And Codes
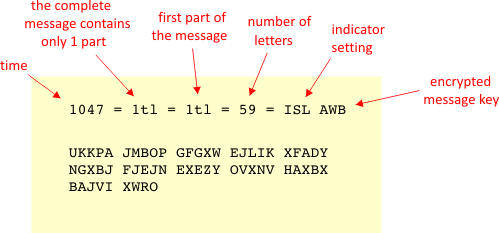



Enigma The German Cipher Machine
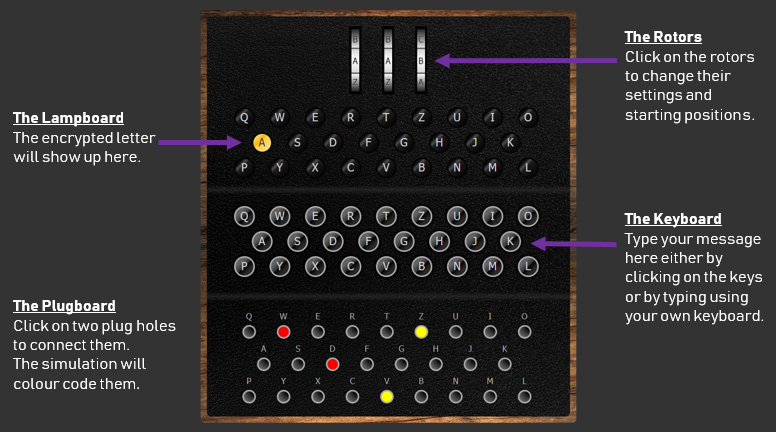



Enigma Machine By 101computing Net




10 Codes And Ciphers Commonly Used In History Ciphers And Codes Coding Cryptography



Enigma
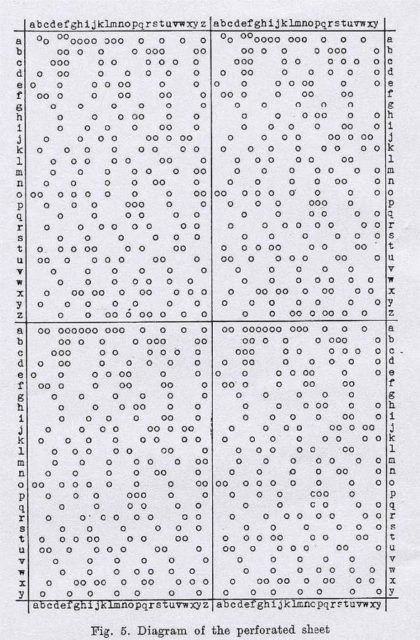



Polish Codebreakers Cracked Enigma In 1932 Before Alan Turing




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium
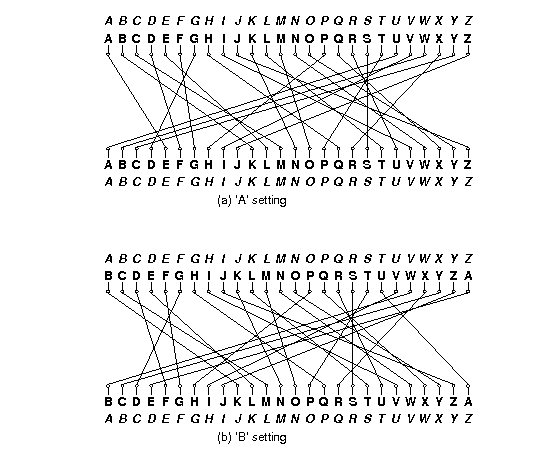



Project 1 Cs 61b Fall 19




The Enigma Cipher Machine And Breaking The Enigma Code




Secret Codes For Writing Codes And Ciphers Ciphers And Codes Coding Encrypted Messages




Enigma Machine Brilliant Math Science Wiki




The National Archives Here S Something To Get Your Brain Working This Mondaymorning Encrypt And Crack A Code Using Alan Turing S Probability Based Method You Ll Need A Pencil Paper Scissors
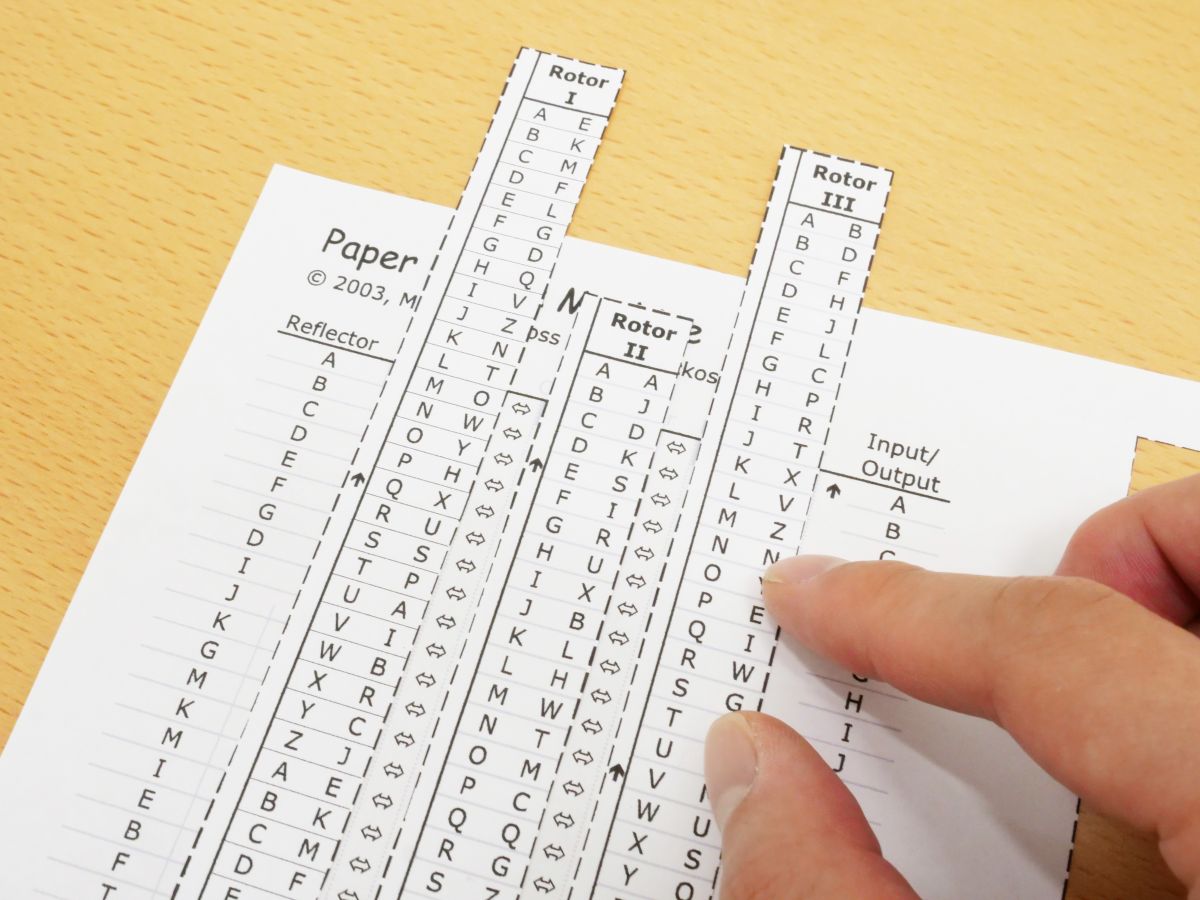



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine
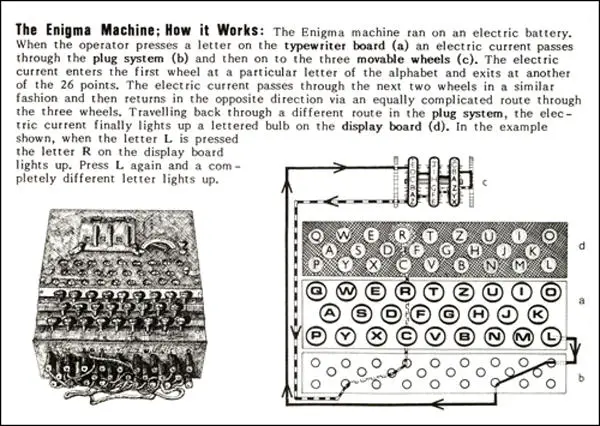



Enigma Machine



Enigma Procedure



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf




Substitution Cipher Png Images Pngegg




Project 1 Enigma




Enigma Technology And The History Of Computers




Enigma Key Book Photo From Authentic German Codebook From Before Download Scientific Diagram




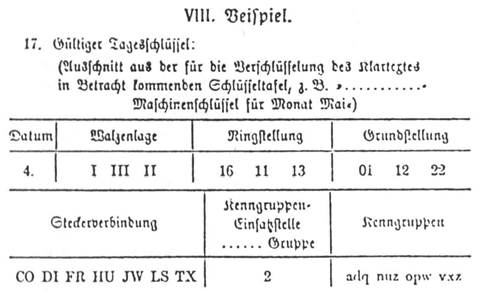
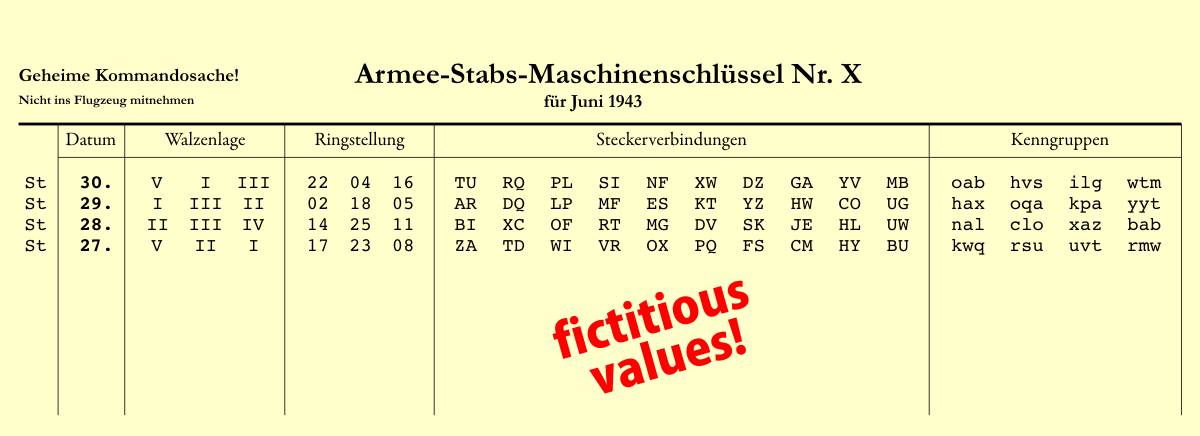
Enigma Daily Settings Generator 101 Computing
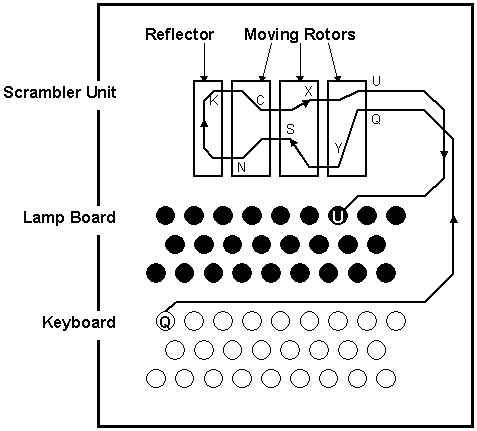



Enigma And A Way To Its Decryption




The Enigma 1




Enigma Machine Brilliant Math Science Wiki




Codes And Ciphers Puts Students To Test Bryn Mawr Alumnae Bulletin



0 件のコメント:
コメントを投稿